{{ slotProps.page.h1_title }}

Beautiful Creative Solutions
Aliquam a augue suscipit, luctus neque purus ipsum neque dolor primis a libero tempus, blandit and cursus varius and magnis sapien

Friendly Interface
Feugiat primis ultrice semper lacus cursus feugiat undo primis ultrice a ligula an auctor tempus magnis

Extremely Flexible
Feugiat primis ultrice semper lacus cursus feugiat undo primis ultrice a ligula an auctor tempus magnis
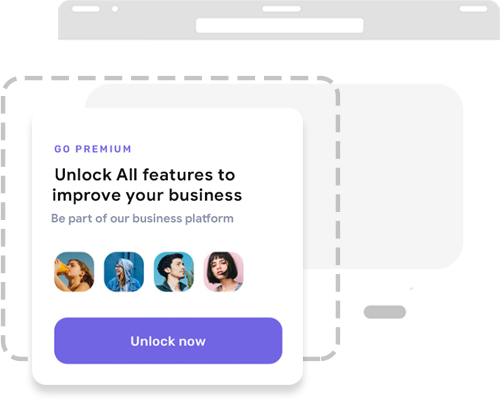
Easy To Customize
Feugiat primis ultrice semper lacus cursus feugiat undo primis ultrice a ligula an auctor tempus magnis
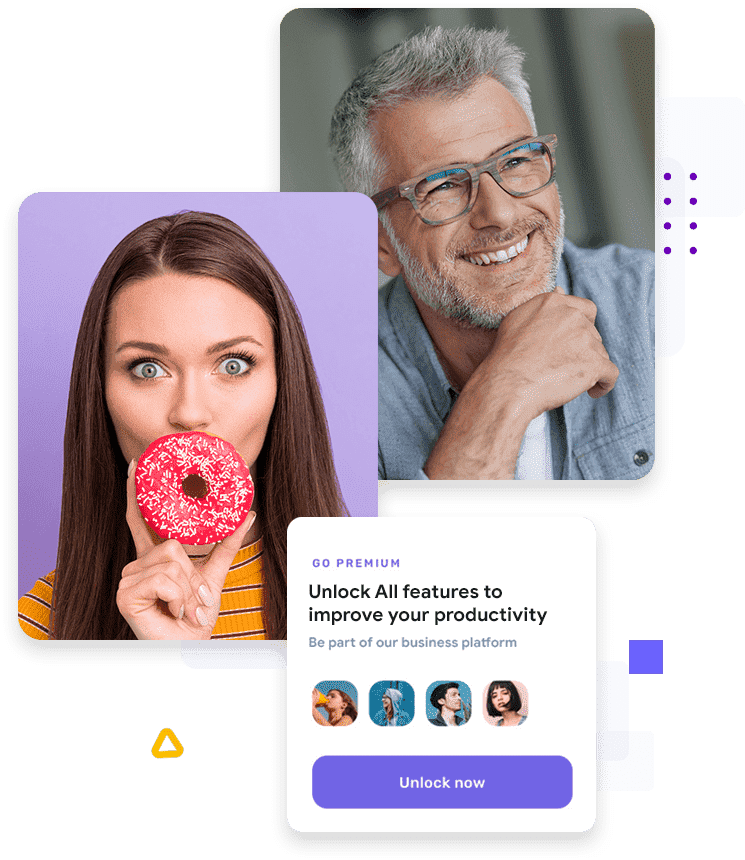
Work smarter with powerful features
Quaerat sodales sapien euismod blandit purus a purus ipsum primis in cubilia laoreet augue luctus magna dolor luctus and egestas sapien egestas vitae nemo volute
Friendly Interface
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
Powerful Options
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
File Manager
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
Convert Media Files
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
Files Sharing
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
Extensions & Addons
Porta semper lacus cursus feugiat primis ultrice ligula risus at auctor tempus feugiat impedit felis undo auctor augue mauris
Got Questions? Look Here
Aliquam a augue suscipit, luctus neque purus ipsum neque dolor primis a libero tempus, blandit and cursus varius and magnis sapien
Can I see PoolsDrive in action before purchasing?
Etiam amet mauris suscipit in odio integer congue metus vitae arcu mollis blandit ultrice ligula egestas and magna suscipit lectus magna suscipit luctus blandit vitae
What are the requirements for using PoolsDrive?
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
Can I use PoolsDrive on different devices?
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
Can I use PoolsDrive on different devices?
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
Do you have a free trial?
Cubilia laoreet augue egestas and luctus donec curabite diam vitae dapibus libero and quisque gravida donec and neque. Blandit justo aliquam molestie nunc sapien
How does PoolsDrive handle my privacy?
Etiam amet mauris suscipit sit amet in odio. Integer congue leo metus. Vitae arcu mollis blandit ultrice ligula
I have an issue with my account
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
I have an issue with my account
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
I have an issue with my account
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
I have an issue with my account
An enim nullam tempor sapien gravida a donec ipsum enim an porta justo integer at velna vitae auctor integer congue undo magna at pretium purus pretium
Have More Questions? Read Our Knowledge Base
Choose a Pricing Plan
Take a FREE 30 Day Trial. No Credit Card Required. Affordable monthly and yearly billing plans make owning a website more affordable than ever before.
Basic
Save 20%
$1,299.99 a year
1 Project
Contact form
5 GB of Storage
Basic Support
Advanced
Save 20%
$2,999.99 a year
Up to 3 Projects
10 GB of Storage
Premium Support
Contact Form With CRM
Professional
Save 20%
$4,999.99 a year
Up to 5 Projects
15 GB of Storage
Premium Support
Contact Form With CRM
Need more projects, more storage or customization of your websites? Contact us for pricing on a completely custom package tailored to your specific needs.
Accepted Payment Methods
Money Back Guarantee
Try Before You Buy Explore PoolSite.AI Basic for up to 30 days. No credit card necessary to test drive our product.
SSL Encrypted Payment
Your information is protected by 256-bit SSL encryption.
Ready to Join PoolsDrive?
Donec vel sapien augue integer urna vel turpis cursus porta, mauris augue luctus dolor velna auctor congue tempus
Start a 30 Day FREE Trial
